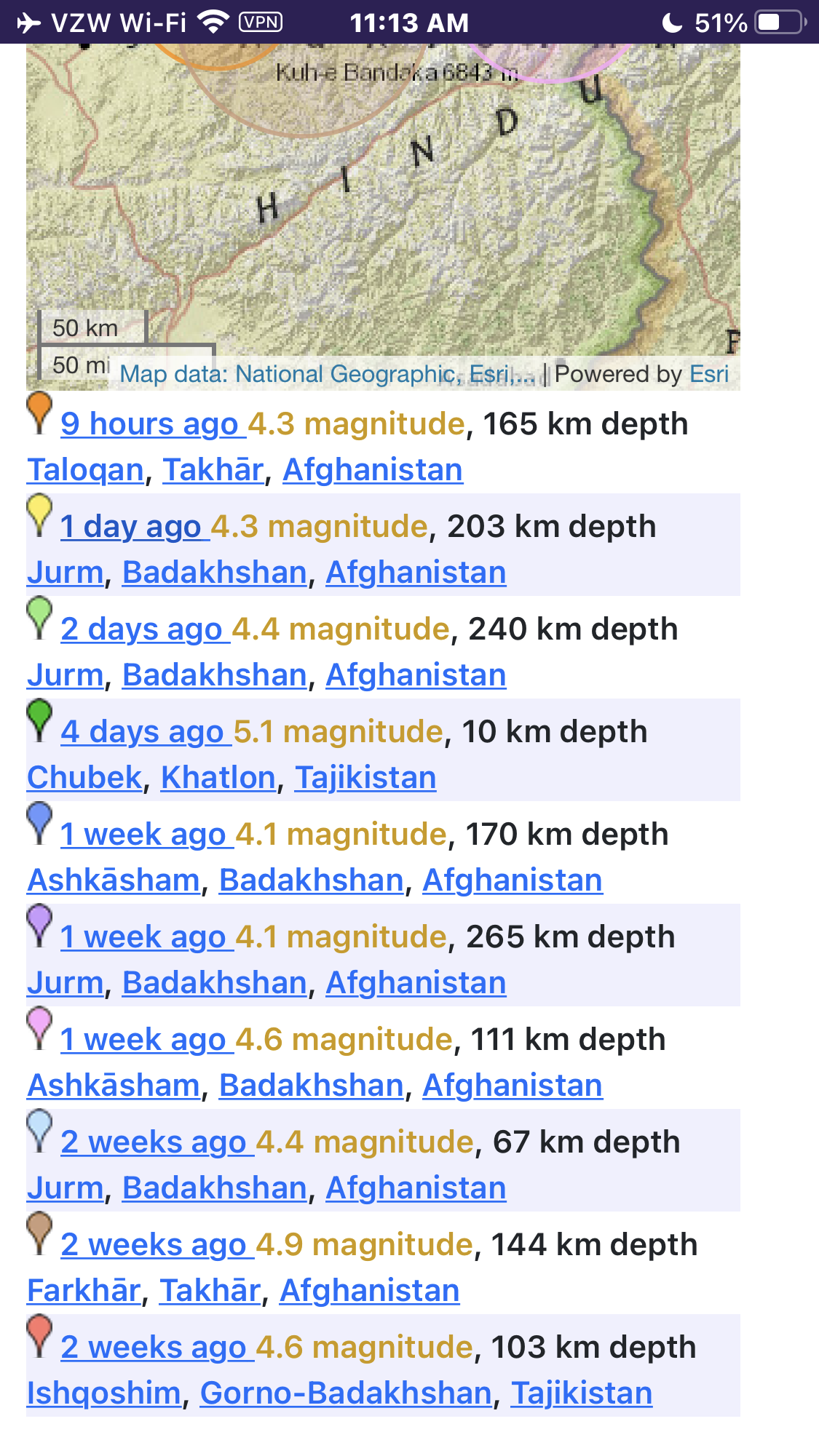
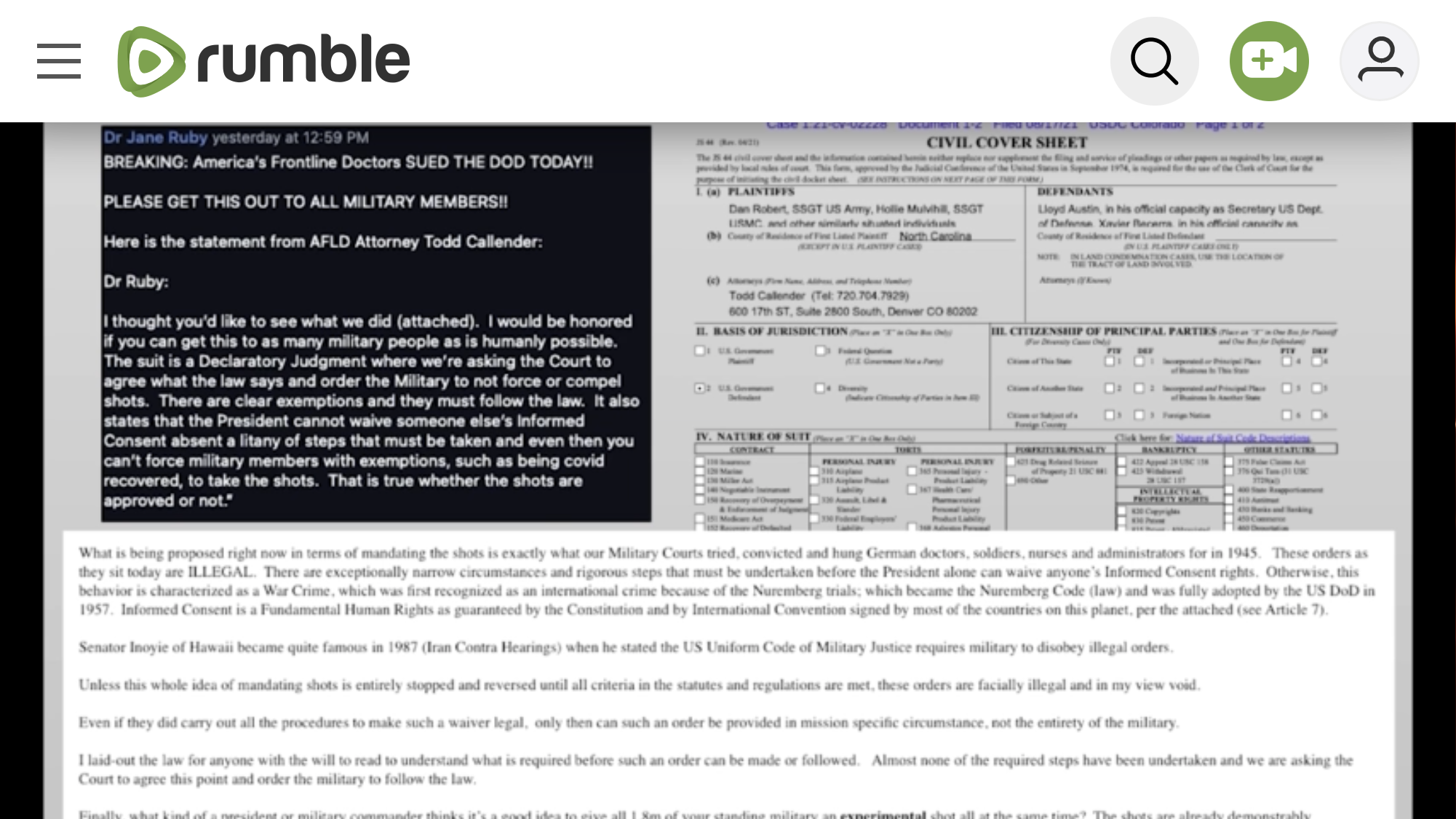
Have we advanced to the part of the sting where we will be seeing so called good guys washed out. I’m not saying I know who’s who, but it sure is getting confusing.
Gotta dig here people
We are going to have a mob of angry people when we all realize the true extent of EVERYTHING the med treats....not just COVID, aka. the weaponized flu and vaxx reactions for many; Epstein-Barr, mono nucleosis, some breast Cancer, ovarian ca, and so much more. Consider this, it stops pathogen replication so the earlier you take it the better.
And damn all these filthy “foods” and toxins in our cleaning supplies, body products, clothing. I think of all the sugar, the alcohol and smoking promotions,...the combined effects of which make it so very difficult for the body to remove it all.
Add stress and fear, and the divisive tactics that make so many angry and isolate(d). Our bodies need some help! Maybe Ivermectin prophylaxis is needed for until we sort out the full extent of the evil war waged against us.
I did an interview of a woman who had post polio syndrome. She give me stacks of research on it. She wanted people to know there was a danger. (I was doing some journalism part time. This was about 1996-7. So newspapers were the only widely available media then.)
That research opened my eyes again.
I remember reading how some child care workers and nannies would care for newly vaccinated babies and develop when exposed to bodily wastes.
Like many people here, I’ve seen a lot of stuff. This awakening is so amazing. I am finding more and more people I can relate with versus the standard asleep sheep, who move through life blind, numb and afraid to analyze reality.
I managed a Birth to Three Program, early intervention. The State demanded we keep records and report on the vax status of the kids. I had a huge detailed spreadsheet listing every possible jab they gave to the babies and toddlers.
We would not get our grant funding unless the sheet was turned in so my company was very strict about the reporting.
I completed that report 3 years in a row and I saw two trends. Federally sponsored State administered HUSKY insured kids had more vax requirements than the commercially insured, like CIGNA etc. The HUSKY insured were also given multi vax cocktails.
Keep in mind, B23 and early intervention is for disabled kids, etc. Babies and toddlers with significant delays in development. IMHO, what a freakin feedback loop.
Something else I noticed in recent years: pregnant mothers were being told they “needed” vaccines!! This was always considered a big no-no.
Now I have clients who were given the CoVid infusions while pregnant. The trend is insist the vax be given to the moms on HUSKY.
Yup, those records disappeared from the pediatricians office, from Yale where we went via ambulance, where they attempted to physically remove me from her bedside to do a blood work, which I approved but the spinal tap that I refused to authorize. (I called the police and the pediatrician to stop them and it worked.)
Imagine these companies demanding the jab and charging people for tests or surcharging them for not being vaxxed, also being able to file for death benefits upon the death of their employees???
Comity Comity is the courtesy one jurisdiction gives by enforcing the laws of another jurisdiction. Comity is granted out of respect, deference, or friendship, rather than as an obligation. In American constitutional law, comity has arisen in two ways. Historically important was the failure of comity in interstate relations. In the modern context, comity is usually an issue that involves the federal courts’ willingness to rule on a state law in the absence of decision by a state court on the same issue.
In law, comity specifically refers to legal reciprocity, the principle that one jurisdiction will extend certain courtesies to other nations, or other jurisdictions within the same nation. This is particularly done by recognizing the validity and effect of their executive, legislative, and judicial acts. The term refers to the idea that courts should not act in a way that demeans the jurisdiction, laws, or judicial decisions of another jurisdiction. A presumption that other jurisdictions will reciprocate the courtesy shown to them is a part of comity. Many statutes relating to the enforcement of foreign judgments require that the judgments of a particular jurisdiction will be recognized and enforced by a forum only to the extent that the other jurisdiction would recognize and enforce the judgments rendered by that forum.
In the law of the United States, comity may refer to the Privileges and Immunities Clause in Article Four of the United States Constitution. This clause provides that “The Citizens of each State shall be entitled to all Privileges and Immunities of Citizens in the several States.”
However, in judicial context, comity should not be misinterpreted as implying that all laws are of universal jurisdiction. In many countries, comity is effective only to the extent that foreign laws or judgments do not directly conflict with the forum country’s public policy.
The concept of comity has often led US courts to adopt outcomes that either encourage both US and foreign firms to evade US regulation or to accept broad discretionary authority in the executive branch at the expense of legislative controls.
States usually as a matter of reciprocity and comity:
allow visitors to drive cars with drivers’ licenses from other states, recognize marriages and adoptions in other states, and often grant professional licenses to migrants or visitors.
Moreover, the concept of comity has led to the modern doctrine of abstention, which stems from the notion that the state and federal courts are equally obligated to enforce the United States Constitution.
Where uncertain questions of state law must be resolved before a federal constitutional question can be decided, federal courts should abstain” from reaching a decision on federal issues “until a state court has addressed the state questions” [i].
Likewise, on grounds of comity and pursuant to federal law, the Supreme Court has generally refused to allow federal courts to intervene in pending cases in state courts where there is no evidence of bad faith harassment.
Comity is “a proper respect for state functions, a recognition of the fact that the entire country is made up of a Union of separate state governments,
and a continuance of the belief that the National Government will fare best if the States and their institutions are left free to perform their separate functions in their separate ways.” Usually, this is referred to as ‘Our Federalism’[ii].
[i] Brockett v. Spokane Arcades, Inc., 472 U.S. 491 (U.S. 1985)
[ii] Younger v. Harris, 401 U.S. 37 (U.S. 1971) (1971)
It has been an extremely difficult week as the world has watched the collapse of the Afghan government. For our service members, veterans, and their families, it has been especially frustrating and heart wrenching to see, after twenty years of American sacrifice, Afghan security forces concede with such little resistance, and to see so many of our Afghan interpreters and allies still trapped.
I’ve attended several briefings this week with both the State Department and DOD, and next week, my colleagues and I in the House will come together in a bipartisan briefing to hear directly from Secretary of State Antony Blinken, Secretary of Defense Lloyd Austin, Chairman of the Joint Chiefs of Staff General Mark Milley, and others. Just this afternoon, General Milley stated that 5,734 people have been evacuated in the last 24 hours. This is an improvement, although it is still far from satisfactory. I’ll be back to provide you with the latest following that briefing.
Locally, my staff is diligently working on requests we’ve received from constituents who have contacted my Norwich office about help with Afghan Special Immigrant Visa applications. If you’re an eastern Connecticut resident and need assistance for yourself or another individual who has an SIV application pending, or is awaiting the issuance of a travel document, click here or call us at 860-886-0139.
I’ve joined my colleagues on both sides of the aisle to advance efforts to expand and speed up the SIV application process, and right now the focus needs to be on helping our people and our allies in Afghanistan to get out safely. If you have questions, please contact my office.
Now here with a few updates from the week.
What is our plan to ride out the Storm we begged for to begin?
Let’s go!!
We got this!
Election cybersecurity is an urgent matter of national security. Under our time-honored system, implementing the necessary defenses falls to states and local governments. We must not leave them to face the threat of powerful foreign adversaries unaided. Congress should provide for the common defense by equipping states with the resources they need to deploy robustly auditiable paper ballots, risk-limiting audits, and other cybersecurity improvements. With your leadership, elections in 2020 and beyond can be well secured, and voters will have good reason to have confidence in the results. But if we delay action, I fear it is only a matter of time until a national election result is disrupted or stolen in a cyberattack.
J Alex Haberman. https://jhalderm.com/pub/misc/fsgg-voting-written19.pdf
U.S. House Appropriations Subcommittee on Financial Service and General Government “Election Security: Ensuring the Integrity of U.S. Election Systems” February 27, 2019 Statement of Dr. J. Alex Halderman Professor of Computer Science and Engineering, University of Michigan Director, Michigan Center for Computer Security and Society Chairman Quigley, Ranking Member Graves, and distinguished members, thank you for the opportunity to testify about this urgent matter of national security. Three years ago, the United States Presidential election was attacked. Hackers penetrated political campaigns and leaked internal communications online, they manipulated social media in an effort order to sow discord, and they targeted our election infrastructure, including voter registration systems in at least 18 states. These attacks were about more than undermining voter confidence. In the assessment of the Director of National Intelligence, they marked a “significant 1 After two years of investigation by Congress and the intelligence community, we know that the attackers had the capability to do even more damage than they did. The Senate Select Committee on Intelligence has concluded that in some states, attackers “were in a position to, at a minimum, alter or delete voter registration data.”2 Had they done so (and had it gone undetected), there would have been widespread chaos on Election Day, as voters across the vulnerable states showed up to the polls only to be told they weren’t registered. We were spared such a blow to the foundations of American democracy only because Russia chose not to pull the trigger. Next time, things could be much worse, and it’s not just voter registration systems that are at risk: the nation’s voting machines are stunningly vulnerable to attacks that could sabotage the voting process or even invisibly alter tallies and change election outcomes. I know because I have developed such attacks myself as part of over a decade of research into election security 3 threats and defenses. Last fall, Chairman Quigley and Representative Katko invited me to demonstrate such an attack at a briefing on Capitol Hill. I brought a touch-screen voting machine used in 18 states, and we held a small mock election. I remotely hacked the voting machine to 4 Office of the Director of National Intelligence, “Assessing Russian Activities and Intentions in Recent US Elections”, January 2017. https://www.dni.gov/files/documents/ICA_2017_01.pdf 2 Election: Summary of Initial Findings and Recommendations”, 2018. https://www.burr.senate.gov/imo/media/doc/RussRptInstlmt1-%20ElecSec%20Findings,Recs2.pdf 3 4 escalation” of foreign “efforts to undermine the U.S.-led liberal democratic order”. steal both Congressmen’s votes and changed the election winner. 1 U.S. Senate Select Committee on Intelligence, “Russian Targeting of Election Infrastructure During the 2016 My curriculum vitae and research publications are available online at https://alexhalderman.com. I demonstrated a similar attack for The New York Times, as shown in this video: https://www.nytimes.com/video/opinion/100000005790489/i-hacked-an-election-so-can-the-russians.html 1
This level of vulnerability is endemic throughout our election system. Cybersecurity experts have studied a wide range of U.S. voting machines, and in every case, we’ve found problems that 5 Some people think that the decentralized nature of the U.S. voting system and the fact that voting machines aren’t directly connected to the Internet make interfering in a state or national election impossible. Unfortunately, that isn’t true. Some election functions are actually quite centralized, and our election infrastructure is not as distant from the Internet as it may seem. Before every election, voting machines and optical scanners need to be programmed with the design of the ballot, the races, and candidates. Election workers create this programming on a central computer called an election management system, then transfer it to voting machines using USB sticks or memory cards. Hackers who compromise an election management system can hijack the ballot programming process to spread a voter-stealing attack to large numbers of machines. Election management systems are often not adequately protected, and they are not always properly isolated from the Internet. Moreover, a small number of election technology vendors and support contractors program and operate election management systems used by many local governments. The largest of these services over 2000 jurisdictions spread across 34 states. Attackers could target one or a few of these companies and spread an attack to election equipment that serves millions of voters. Furthermore, in close elections, decentralization can work against us. An attacker can probe the most important swing states or swing districts for vulnerabilities, find the areas that have the weakest protection, and strike there. In a close election, changing a few votes may be enough to tip the result, and attackers can choose where—and on which equipment—to steal those votes. Fortunately, we know how to better defend election infrastructure and protect it from cyberattacks in 2020 and beyond. There are three essential measures:
-
First, we need to replace obsolete and vulnerable voting equipment, such as paperless systems, with optical scanners and paper ballots—a technology that 30 states already use statewide. Paper ballots provide a resilient physical record of the vote that simply can’t be compromised by a cyberattack.
-
Second, we need to consistently check that our election results are accurate, by inspecting enough paper ballots to tell whether the computer results from the optical scanners are right. This can be done with what’s known as a risk-limiting audit (RLA). Such audits are a common-sense quality control. By manually checking a random sample of the ballots, officials can quickly and affordably provide high assurance that the election outcome is correct. 5 would allow attackers to sabotage machines and alter vote tallies. For an accessible introduction to election cybersecurity, see my online course, Securing Digital Democracy, which is available for free on Coursera: https://www.coursera.org/learn/digital-democracy. 2
-
Lastly, we need to raise the bar for attacks of all sorts—including both vote tampering and sabotage—by applying cybersecurity best practices to the design of voting equipment and registration systems and to the operation of computer systems at election offices. 6 These are not simply my recommendations. Paper ballots, manual audits, and security best practices are a prescription endorsed by the overwhelming majority of election security experts, 7,8 and by the National Academies of Science, Engineering, and Medicine. also widely favored by election officials. These measures are Many states have begun to implement these improvements using the $380 million in election cybersecurity funding that Congress appropriated last year. According to the Election Assistance Commission, states intend to use 36% of this funding ($136 million) for cybersecurity improvements, 28% ($103 million) for purchasing new voting equipment, and 6% ($21 million) 9 for improving election audits. These are necessary, appropriate, and urgent priorities. However, much more needs to be done before Americans go to the polls in 2020. Although some states have made significant progress towards securing their election infrastructure, other have barely gotten started, and the nation as whole remains a patchwork of strength and weakness. In 2018, 41 states used voting machines that were at least a decade old, and some, including parts of Pennsylvania and New Jersey, used machines dating from around 1990. Forty-three states used machines that are no longer manufactured, forcing election officials to cannibalize old machines for spare parts or even turn to eBay. Twelve states10 still make widespread use of paperless direct-recording electronic (DRE) voting machines, which are impossible to reliably audit to detect potential errors or malfeasance. All of Georgia, for example, voted in November using the same model of vulnerable paperless DRE that I hacked in front of Chairman Quigley last fall. After years of underinvestment, America’s election infrastructure is crumbling, and the $380 million can only serve as a down payment towards fixing it. Many states would like to replace vulnerable and obsolete voting equipment before 2020, but they are struggling to figure out how to pay for it. Pennsylvania, for instance, plans to switch from insecure paperless machines to paper ballots, but the state’s share of last year’s HAVA 6 office. He made the point well in 2016: “There’s something really nice about the old paper-ballot system. You don’t worry about hacking.” http://www.businessinsider.com/donald-trump-election-day-fox-news-2016-11 7 8 9 https://www.eac.gov/news/2018/08/21/state--territories-plan-to-spend-majority-of-hava-grant-funds-on-election-sec urity-system-upgrades/ 10 President Trump himself has consistently endorsed the use of paper ballots, both as a candidate and since taking National Academies of Science, Engineering, and Medicine, “Securing the Vote: Protecting American Democracy”, 2018. https://www.nap.edu/catalog/25120/securing-the-vote-protecting-american-democracy Additionally, the National Institute of Standards and Technology (NIST) has concluded that it is not possible to effectively audit a voting system to detect and correct potential hacking without a voter-verified paper ballot. U.S. Election Assistance Commission, “EAC Releases 48 HAVA Grants State Plans, Budgets,” August 2018. The twelve states with large numbers of paperless DRE voting machines are: Delaware, Georgia, Indiana, Kansas, Kentucky, Louisiana, Mississippi, New Jersey, Pennsylvania, South Carolina, Tennessee, and Texas. Eight additional states use DREs with a voter-verifiable paper audit trail (VVPAT), an obsolete kind of paper backup: Arkansas, California, Illinois, Ohio, North Carolina, Utah, West Virginia, and Wyoming. Verified Voting maintains an online database of the equipment in use in each locality: https://www.verifiedvoting.org/verifier/. 3
funds was $13.5 million, only about 25% of the cost of implementing hand-marked paper ballots across the state. Georgia’s share was $10.3 million, less than a third of what it needs just to replace its paperless machines. Without further federal assistance, we risk that new equipment and other critical improvements won’t be in place for many years. With the 2020 election on the horizon—the next major target for foreign cyberattacks—we need to act before it’s too late. What will it cost to fix the problem? The highest priority should be to replace DRE voting 12 It’s important to understand that states can choose from several kinds of voting equipment, and that these choices greatly affect the overall cost and the security achieved. Fortunately, the most cost effective approach is also the most secure: hand-marked paper ballots counted using optical 13 In many states, there are no rules in place to prevent local governments from spending federal funds on insecure and unauditable kinds of voting equipment. Some voting machine vendors continue to market paperless DREs, as well as DREs with so-called “voter-verifiable paper audit trails” (VVPATs)—
(See article for more)