Somewhere with heavy moderation and only quality posts, no hopium, no wins of the week, just deep meaningful research
Something that might act as a base layer to provide meaningful content for the hopium addicts here
imo the noise in here, while much better than voat/qrv was, is still way too much to build a knowledge base that connects different insights
is it possible to create new .win‘s as a user?
many anons are struggling between „trusting the plan“, taking another dose of Hopium or Trustium, and „shilling“ or „dooming“ because of a lack of understanding the underlying strategies at play.
Please everyone interested read this document (as it was referenced by q): https://2009-2017.state.gov/documents/organization/119629.pdf
Q is essentially part of a COIN-strategy. A COIN (Counterinsurgency) strategy, namely the „information component“ [Page 17]. Information Component: Information (acquiring knowledge and exerting influence) is the base component for all other activities, providing the linkages that allow discrete functional elements to cooperate as an integrated whole.
There are 4 Components: (1) Information, (2) Economic and Development, (3) Security, (4) Political Strategy Which are used to gain and hold control (in a positive way) over the population.
Insurgency can be defined as ‘the organized use of subversion and violence to seize, nullify, or challenge political control of a region.‘ [page 12]
Communist insurgency can then be defined as the organized use of subversion and violence to obtain political control of a nation.
So, i dont think anything „BOOM“ is going to happen in the next 3 years. Not dooming here, there probably is a big plan and you can trust it, but you have to actually be patient.
Communist Insurgency is a ~20 year strategy. Any counter strategy, or „the plan“ - if the insurgency reaches the top of the political hierarchy (which it did) - will take at least a whole generation to wipe it out and ANOTHER GENERATION to rebuild trust of political and media institutions.
So, good luck datefagging - the plan is going to drag out for at least 15 years.
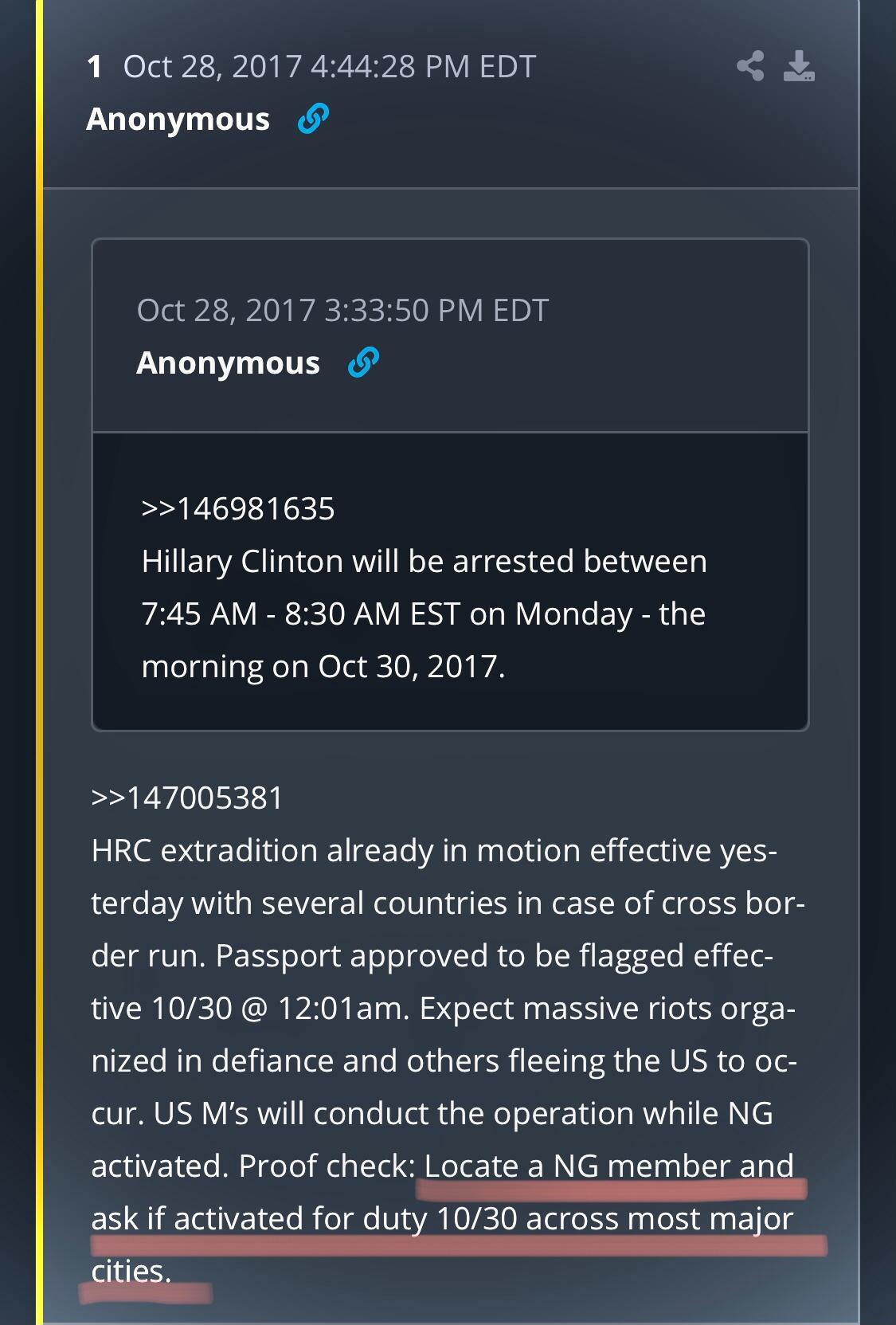
While browsing through some Q posts, i‘ve noticed that many have hashes as image file names.
For example: Post 1202
For non-techies: Hashes are one-way functions that take any input text and transform it to an encrypted text, which (ideally) cannot be reversed.
However, the hash in 1202 seems to be md5 (a hashing algorithm) and it should be possible to decipher it via bruteforce (trying every combination of words/letters).
Is there any list of decrypted hashes from Q‘s drops?
If not, maybe we should start digging.. Because, after all, we already have more than we know