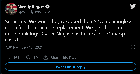
Wendy Rogers: "Summary: We won. They dropped their $2.8 meaningless claim for the machine replacement. We get the routers and Splunk logs. Cyber Ninjas has full access. Maricopa caved."
(media.greatawakening.win)
👨🏫 AUDIT AUDIT AUDIT 🛠️
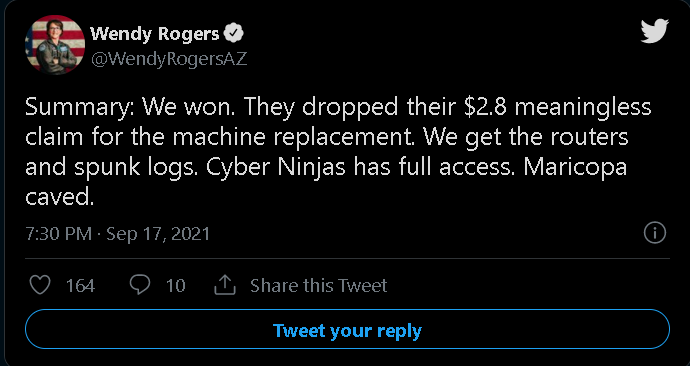
I don't think many people realize even if the routers were wiped the Splunk logs will show all the traffic..
Routers don't keep logs anyway. There's simply not enough space on them. It's the config that matters. The splunk logs has all the goodness. The question is what's the retention, 6 months is the average.
Also, most places keep their router config is some sort of backup system with version control. Do they have access to that?
They do keep router tables which are the rules for what traffic is allowed through which networks.
Routing tables contain known networks and their path. These can be dynamically learned through routing protocols (OSPF, EIGRP, LISP) or statically set. The former being lost on reboot. The voting machines will likely be attached to an existing network so this isn't really important. I believe what you are mean to refer to are access-lists, and they are likely going to be the most important configuration detail on those routers.
Access-lists can be used for allowing, denying, or routing specific traffic. They are manually configured and will be retained on the startup configuration if saved. These can also generate logs on the actual router (which will be lost on reboot or power loss) or be used in conjunction with a network based monitoring software such as Splunk. Having any access-lists which allow traffic from an IP range of a foreign nation just adds to the whole situation. It would be even worse if it was specifically allowing traffic to the same subnet the machines were on.
Something to remember: they denied they had any network connectivity at the beginning. Now they have lost the fight retaining the routers. If they failed to remove that configuration it will be trouble. If they succeeded and those configuration files are missing it will still be suspect. If they overwrote the configuration and the router saves the date/time (usually requiring a different protocol, NTP, running so it actually knows), that will also be suspect.
Adding the Splunk logs to this (which, as I understand, can potentially store logs for at least 6 years) just gives more opportunities for us to catch the slimy fucks.
Thanks for explaining