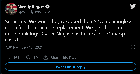
Wendy Rogers: "Summary: We won. They dropped their $2.8 meaningless claim for the machine replacement. We get the routers and Splunk logs. Cyber Ninjas has full access. Maricopa caved."
(media.greatawakening.win)
👨🏫 AUDIT AUDIT AUDIT 🛠️
Routers don't keep logs anyway. There's simply not enough space on them. It's the config that matters. The splunk logs has all the goodness. The question is what's the retention, 6 months is the average.
Also, most places keep their router config is some sort of backup system with version control. Do they have access to that?
They do keep router tables which are the rules for what traffic is allowed through which networks.
Routing tables contain known networks and their path. These can be dynamically learned through routing protocols (OSPF, EIGRP, LISP) or statically set. The former being lost on reboot. The voting machines will likely be attached to an existing network so this isn't really important. I believe what you are mean to refer to are access-lists, and they are likely going to be the most important configuration detail on those routers.
Access-lists can be used for allowing, denying, or routing specific traffic. They are manually configured and will be retained on the startup configuration if saved. These can also generate logs on the actual router (which will be lost on reboot or power loss) or be used in conjunction with a network based monitoring software such as Splunk. Having any access-lists which allow traffic from an IP range of a foreign nation just adds to the whole situation. It would be even worse if it was specifically allowing traffic to the same subnet the machines were on.
Something to remember: they denied they had any network connectivity at the beginning. Now they have lost the fight retaining the routers. If they failed to remove that configuration it will be trouble. If they succeeded and those configuration files are missing it will still be suspect. If they overwrote the configuration and the router saves the date/time (usually requiring a different protocol, NTP, running so it actually knows), that will also be suspect.
Adding the Splunk logs to this (which, as I understand, can potentially store logs for at least 6 years) just gives more opportunities for us to catch the slimy fucks.
This guy networks.
Routerfag coming in hot!
Thanks for explaining
Thank God for industry standards.
Great post
cyber ninjas has the packet data already they just needed to check all the boxes of the aduit which included physical routers
So, the routers send the logs off to another machine which stores the logs. The router doesn't 'keep' them.
Splunk is an application that runs on a server, it could just as easily be something else like Nagios.
The routers export logs to the server which then stores them, they are not stored on the router itself, apart from the most recent ones, depending on the buffer settings.
I didn't say anything about changing them, did you get that from a different post?
Cisco routers can log via the following methods:
Console - Sends logs to the console like a serial port or monitor
Terminal - Sends logs to a VTY session like a ssh or telnet session
Buffer - Which holds a specific amount of log in the router memory; Logs are lost if the router powers off
syslog - This send log messages over UDP to a syslog listener.
if debug is on
Assuming the routers have been turned off since the election, the logs should still be retained... assuming that wherever splunk stores the logs on this system has also been turned off.
Our logs at work are pulled off of our servers by splunk and stored in a separate repository...
Uh, yea they do. Odds are if you look at your home router via Administrative access you will see your up traffic
Commercial routers definitely do, as part of security audits and tracking any corporate espionage. There are logs kept